Starting with luring emails
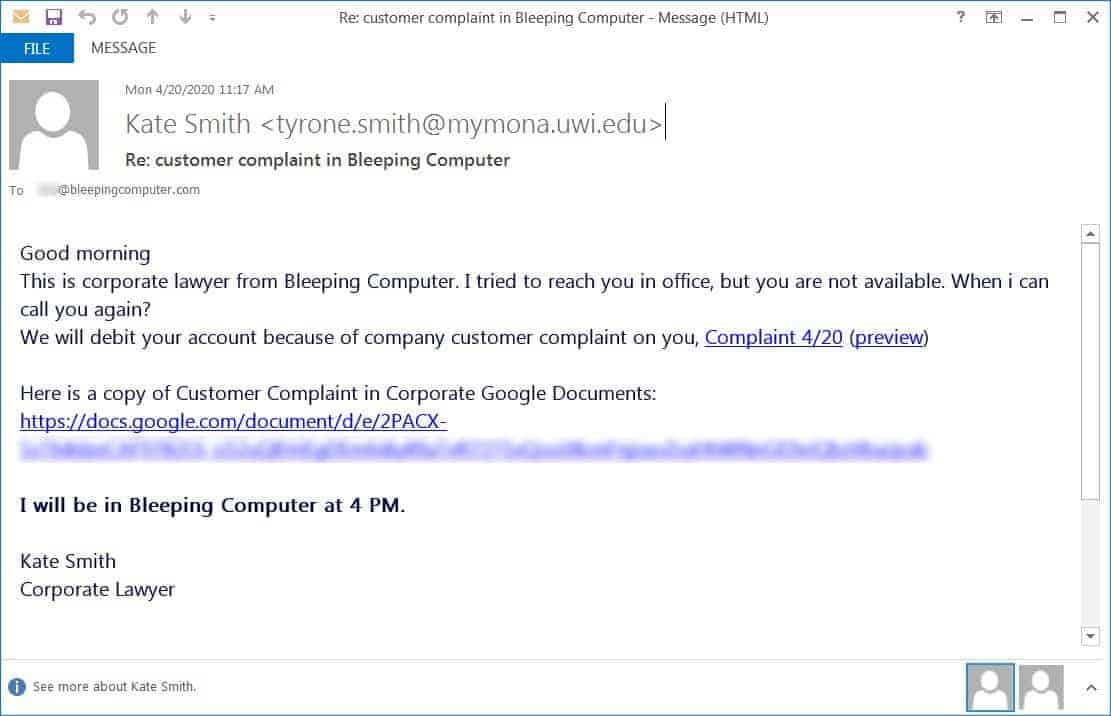
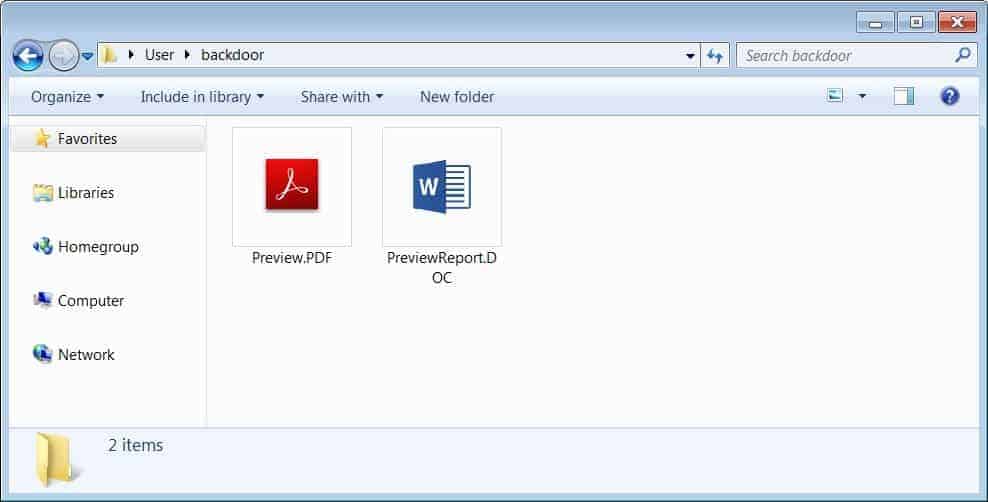
BazarBackdoor begins with a general phishing campaign, which sends emails to employees via the Sendgrid marketing platform. The emails are crafted to be COVID-19 themed payrolls, customer complaints, or employee termination lists, which will be hosted in Google docs. After opening the email, the lures will show up as a word document of PDF, but won’t open and ask the employee to click on their link to view. Here, the campaign is carefully crafted to look familiar as the attackers have designed the landing pages with similar icons of what they’ve sent in emails. This will raise no suspicion to the target. Themes as COVID-19 payroll is set like PreviewReport.DOC and Customer Complaints as DownloadReport.pdf. These are actually executables, as told by James. And since Windows stopped showing the full file extensions, they’re seen as standard DOCs and PDFs by the target.
Going stealthily
The executable is a loader for the backdoor in the system, which, after being clicked, connects to the attacker’s C2 server for procuring the payload. A thing to note here is, this BazarBackdoor trojan contacts the C2 server via Emercoin Decentralized DNS to find the Bazar domain. And since the Emercoin DNS is the only one who uses Bazar hostname and also being decentralized, it’s hard for law enforcement agencies to trace the hostname. After connecting to it, the BazarBackdoor procures the XOR encrypted payload and injects it into the svchost process, stored in C:\Windows\system32\svchost.exe. This is done by using a Process Hallowing and Process Doppelganging, as told by Vitali Kremez. After this, the backdoor will download the Cobalt Strike penetration testing and post-exploitation toolkit on the host system, which is actually used for network security assessment. A cracked version of this tool helps the attackers to gain control, spread across, and even sell access of the entire compromised network to others. This new malware was believed to be developed by the authors of Trickbot malware, as they’re many similarities between these two. Few were found in terms of code, infrastructure, and executable encrypters. Via: BleepingComputer