WordPress Plugin Vulnerability
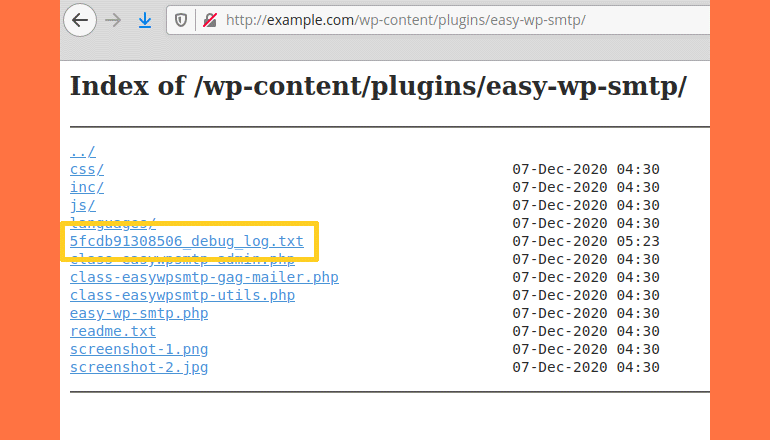
Easy WP SMTP, a plug-in for setting the SMTP configurations for a website’s outgoing emails, has a zero-day bug that’s actively being exploited by hackers. It’s said the plugin has a feature to maintain a record for debug logs. This contains all the logs for email sent from the website, where sensitive data too may be included.
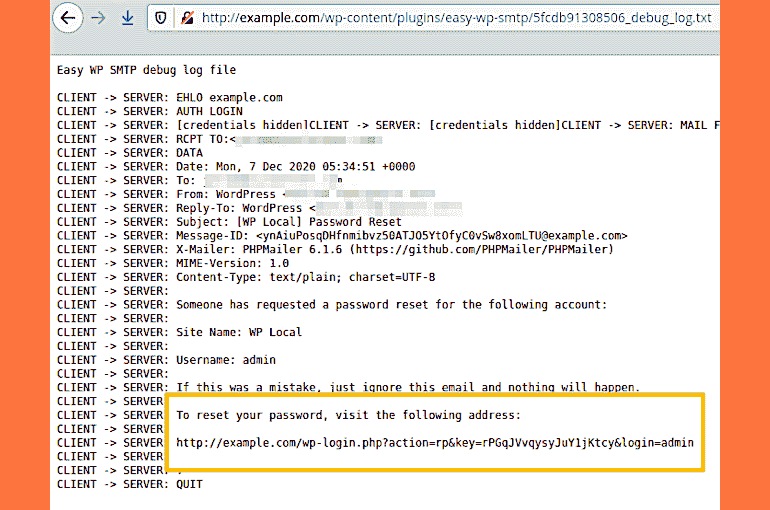
And this is what being targeted by the hackers, as the “plugin’s folder doesn’t have an index.html file, hence, on servers that have directory listing enabled, hackers can find and view the log,” according to NinTechNet‘s Jerome Bruandet. He further elaborated that hackers target sites with vulnerable Easy WP SMTP plugin and attack them to take over the admin accounts through password resetting. Since the password reset works by sending an email with a password reset link within, hackers gaining this link can make a new password for that account.
As the debug files maintain these email content in their logs, accessing these files can let them get the password reset link and use it for making new passwords, eventually taking over the account. Bruandet said the vulnerability is now being exploited and suggested updating the plugin to a new version released on Monday. Easy WP SMTP’s makers have released a new version of it as v1.4.4, which moves the plugin’s debug log to a better-protected area of WordPress logs folder, thus safe. It’s currently unknown how many sites from the 500,000+ have updated this plug-in. Also Read- 300,000+ WordPress Sites Are Open To Administration Access